Storage & Backups Under Attack. This Is What To Do About It
Over the past few months there has been a significant increase in publicized attacks on storage & backup systems, e.g. You can read more about these

Over the past few months there has been a significant increase in publicized attacks on storage & backup systems, e.g. You can read more about these

When it comes to backups, there’s an interesting debate as to whether you should connect your backup systems to Active Directory (AD) or not, and for

What this is about? This time-based attack happens when an attacker manipulates insufficiently-secure time sync configuration to trick the backup systems into thinking that “X” number

On September 27th, Johnson Controls International announced a massive ransomware attack, that encrypted many of the company devices, including VMware ESXi servers. This impacted the company’s

StorageGuard plays a critical role in your cyber resiliency strategy, by helping you increase usage & adoption of your existing data protection tools – and subsequently get more out of your current investment.

In the past two years, cybercriminals have become increasingly skillful at destroying the organizational backup first, only then locking the data – leaving victims no choice but to pay the ransom. Given how long this trend has been around, and the devastating impact of a successful attack, one would expect organizations would get things under control by now. If anything, the situation is worsening.

The ETC Program underscores Dell’s commitment to offer customers flexibility and choice with complimentary solutions such as StorageGuard for protecting their critical systems from cyberattacks and insider threats.

Cyber insurance provides a cushion to fall back on in a successful cyber-attack, providing coverage for damages caused by data loss.

2022 clearly demonstrated that attacks on data represent the greatest cyber-threat organizations face. The attack pace not only continued, it accelerated.
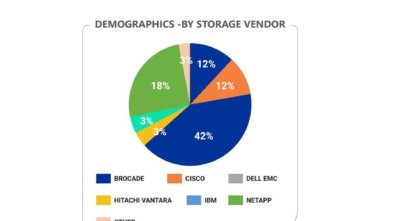
Introduction We analyzed data from a large number of storage risk assessments, to provide a unique insight into the state of storage security. The analyzed data
It’s time to automate the secure configuration of your storage & backup systems.