Secure Configuration of Storage & Backups
Securely Configure Your Storage & Backup Systems – with Configuration Check & Audit
Leading standards require organizations to implement a secure configuration process for each technology. This includes:
- Defining polices, security controls, baseline configuration and technical implementation guides per technology and to periodically update them.
- Validating that all systems adhere to the required configuration baseline and running regular configuration checks to detect drifts and unauthorized changes.
- Reassessing adherence to the baseline after configuration changes or software updates made to the system.
- Automation for configuration documentation, configuration drift detection and response
- Restricting access, rights, interfaces, services and more.
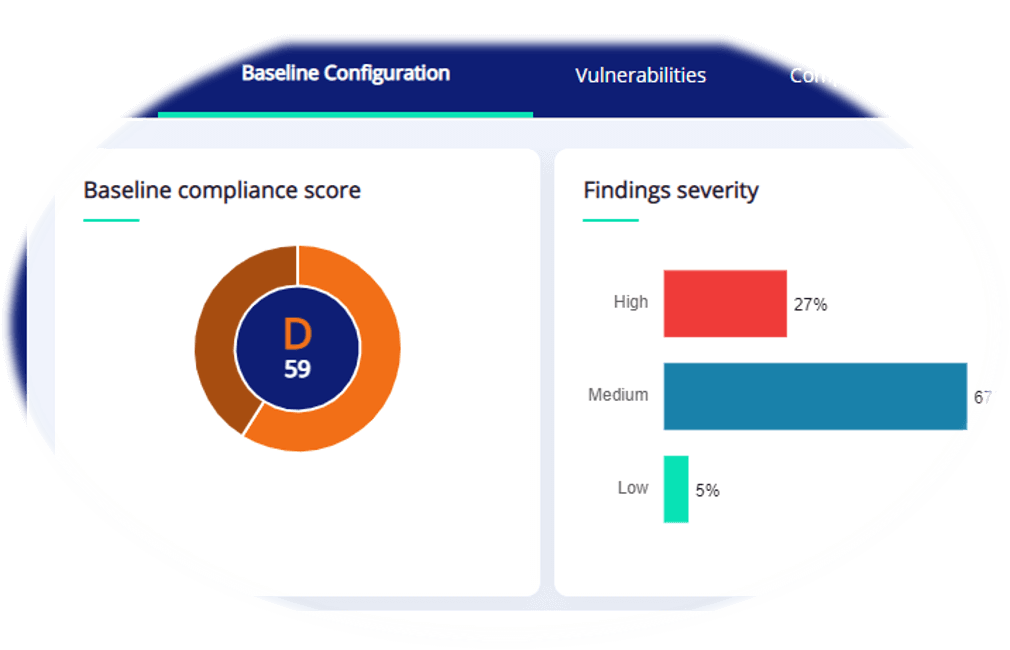
Storage and backup systems are critical IT infrastructure that retains all production data as well as the backup data. Managing baseline configuration and secure configuration process for your storage and backup systems is extremely difficult, since most tools focus on host operating systems and web applications, and are unable to effectively communicate with the rather unique storage and backup technologies.
Best Practice Guide – Setting Secure Configuration Baselines for Storage & Backups
Discover the Ultimate Guide to Setting Configuration Baselines for Storage & Backup Systems.

Product Comparison – Comparing Generic Configuration Tools with StorageGuard
| Secure Configuration and Baseline | Configuration Compliance | |
|---|---|---|
| Endpoint systems | McAfee Endpoint Security | Microsoft Endpoint Manager | Symantec Endpoint Protection | Tanium | CrowdStrike | SCCM | Ivanti Endpoint Manager | Qualys Policy Compliance | McAfee Endpoint Security | Symantec Endpoint Protection | Tanium |
| Applications | | Tenable | Qualys | Rapid7 | Veracode | IBM Security AppScan | Tripwire | Qualys Policy Compliance | McAfee Application Control | AlienVault USM Anywhere |
| Database systems | Imperva | IBM Guardium | McAfee Database Security | Oracle Database Vault | Imperva | IBM Guardium | McAfee Database Security | Trustwave |
| Host systems | Tenable | Qualys | Rapid7 | Tenable | Qualys | Rapid7 | Tanium |
| Storage systems | StorageGuard | StorageGuard |
| Backup systems | StorageGuard | StorageGuard |
StorageGuard Supports These Storage & Backup Systems
FAQs: Secure Configuration Baseline
Find answers to common questions about secure configurations, challenges, and solutions for protecting your storage and backup environments.
What is a secure configuration baseline, and why is it important?
A secure configuration baseline is a set of standardized security settings that ensure systems are configured consistently and securely. For storage and backup systems, it reduces risks from misconfigurations, weak encryption, and unauthorized changes.
What challenges do organizations face in securely configuring storage and backup systems?
Key challenges include the complexity of diverse systems, lack of storage-specific security expertise, reliance on manual processes, and adapting to evolving cyber threats.
How can organizations establish a secure configuration baseline?
Define security baselines with expert input, assess adherence regularly (automated tools like StorageGuard help), prioritize and remediate issues, and generate compliance reports to track progress.
How does StorageGuard help maintain secure configurations?
StorageGuard automates baseline creation, audits configurations, detects unauthorized changes, and provides actionable remediation guidance to ensure systems stay secure and compliant.
Get in touch to run a configuration audit of your storage & backups, and ensure your configuration baseline is met
Talk To An Expert
It’s time to automate the secure configuration of your storage & backup systems.