Compliance & Security Controls for Storage & Backups
Compliance Check & Audit for Storage & Backup Controls - NIST, CIS & ISO
Many organizations must periodically verify that their IT systems comply with numerous industry standards and regulatory requirements. Some of those requirements require certain processes to be in place while others are about configuration settings.
While storage and backup systems are mission-critical IT infrastructure that must comply with requirements, they are extremely difficult to audit given the non-standard operating systems and unique subject matter expertise.
Interpreting requirements for every storage and backup technology is challenging since they each have their own unique terminology, feature set, limitations, command set and application programming interface.
In addition, cross-walking between the various standards and matching the numerous requirements is a hugely complex task.
CISOs Guide To ISO 27040: Storage Security
The release of ISO/IEC 27040:2024 provides an overview, analysis, and guidance for the security of storage & backup systems.

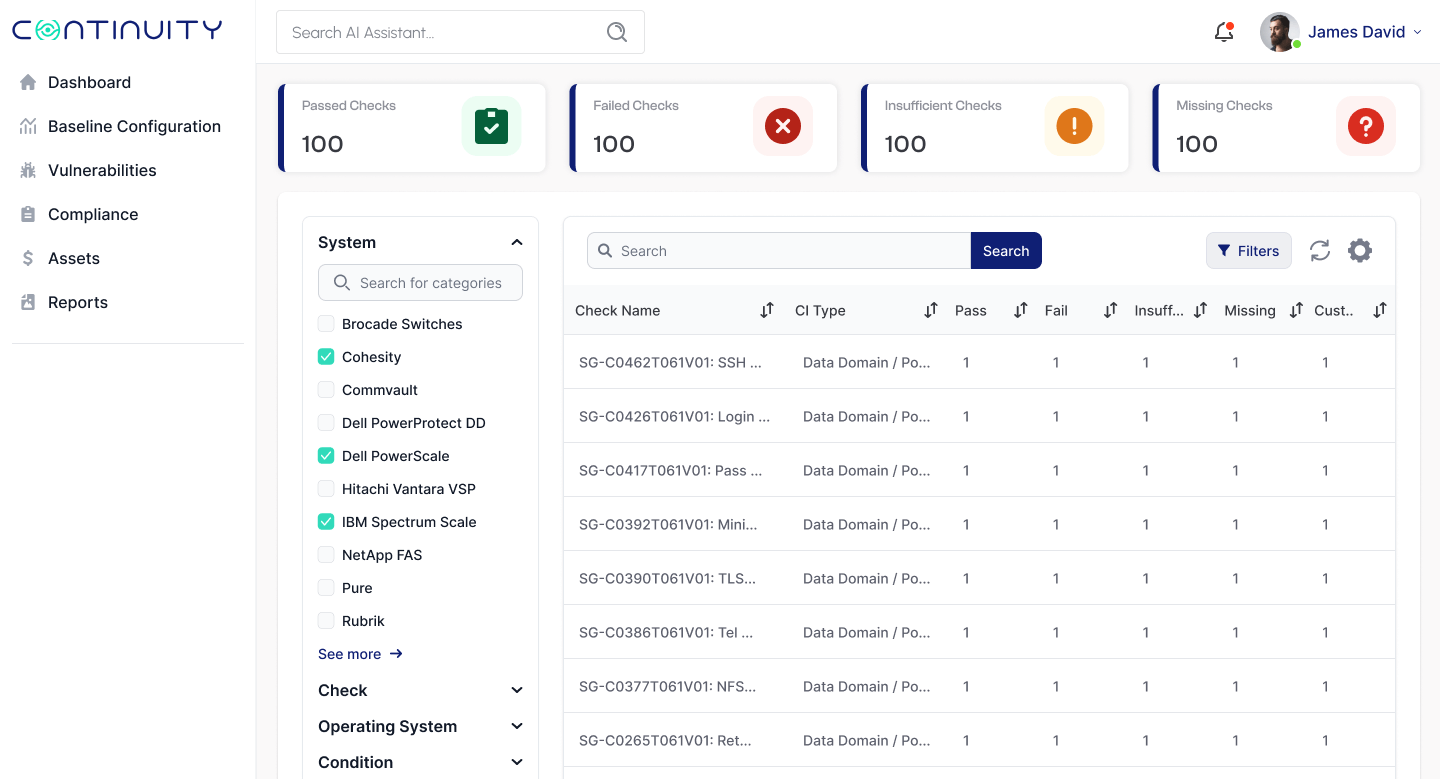
StorageGuard will automatically identify when requirements such as multifactor authentication, encryption of data-at-rest and in-transit, audit logging and restricted access (and many others) are not met.
StorageGuard also performs the following required processes for storage and backup systems:
- Secure configuration process (CIS, NIST baseline security): StorageGuard has out-of-the-box baseline policies by technology, and can automatically identify drifts from the baseline.
- Authenticated vulnerability scan: StorageGuard has a continuously-updated catalog of storage and backup CVE vulnerabilities and detection plugins.
- External assessment: StorageGuard offers an independent assessment of the security posture of Storage and Backup systems based on a vast knowledgebase of best practices and security guidelines
- System inventory: StorageGuard provides a unified view of all storage & backup devices and software components, while automatically mapping storage arrays, storage switches, storage management software, backup clients and other components.
FAQs: Compliance Check & Audit
Find answers to common questions about compliance check & audit for storage & backup controls.
Why is it challenging to run a compliance check on storage and backup systems?
Auditing storage and backup systems is challenging due to their unique operating systems, specialized terminologies, and diverse configurations. Each technology has distinct features and command sets, making standard auditing approaches less effective.
How does StorageGuard assist in ensuring compliance with industry standards?
StorageGuard enables organizations to verify that their storage and backup systems adhere to various standards, including NIST compliance, ISO compliance, CIS compliance, DORA compliance, PCI DSS, HIPAA, and others. It performs scheduled scans using native APIs and CLIs to assess compliance and provides pass/fail reports for each requirement.
What processes does StorageGuard implement to maintain secure configurations?
StorageGuard offers out-of-the-box baseline policies by technology and can automatically identify drifts from these baselines. It maintains a continuously updated catalog of storage and backup CVE vulnerabilities and detection plugins, ensuring systems are securely configured.
Can StorageGuard integrate with existing IT service management (ITSM) solutions?
Yes, when a compliance requirement is not met, StorageGuard reports the finding, which can be viewed within StorageGuard or managed as an incident or problem ticket in ITSM solutions like ServiceNow.
Talk To An Expert
It’s time to automate the secure configuration of your storage & backup systems.