
Continuity Joins Dell Technologies ETC Program to Help Protect Customers’ Storage and Data Protection Systems
About Continuity™
StorageGuard - by Continuity™ - is the ONLY Security Posture Management solution for Storage & Backups, helping to ensure these systems are securely configured, and compliant with industry & security standards.
Storage is becoming a prime target of cybercriminals as they attempt to infiltrate the enterprise.
Faced with a wall of perimeter defenses, security safeguards, and well-patched operating systems and applications, storage and backup systems are now front and center in the fight against ransomware.
According to Gartner[1], ‘Most ransomware attacks target unstructured datasets on network shares, making centralized file storage solutions an attractive target for encryption and/or data exfiltration of large amounts of data.’
The storage attack surface is broader and deeper than many CISOs might suspect. It is tempting to think that storage security concerns could simply be resolved by patching clients (Host Operating Systems) and making sure there’s a backup solution in place. However, cybercriminals can breach storage systems in a number of creative ways.
In the 2023 State of Storage & Backup Security Report, we identified the top five security risks. For each risk, we’ve outlined the business impact. This helps to demonstrate how cybercriminals can get through the parameter to the storage or backup environments.
- Insecure network settings
- Unaddressed CVEs
- Access rights issues (over-exposure)
- Insecure user management and authentication
- Insufficient or incorrect logging and auditing
It’s not just ransomware that’s top of mind for security and storage teams. Auditors and cyber insurance firms are now taking a much closer look at the security of storage & backup systems, as well as regulatory bodies and industry standards.
NIST Special Publication 800-209; Security Guidelines for Storage Infrastructure: ‘Periodically and proactively assess configuration compliance to storage security policy.’
And ISO 27001, published in November 2022, includes the following instruction: ‘Backup copies of information, software and systems shall be maintained and regularly tested in accordance with the agreed topic-specific policy on backup.’
Hardening Dell Storage & Data Protection Systems – with StorageGuard
Dell Technologies is at the forefront of protecting customers’ evolving environments through its PowerProtect portfolio. Through Dell’s Extended Technologies Complete (ETC) program, Dell customers can now add Continuity’s flagship product, StorageGuard, to complement their Dell storage and data protection solutions, helping them keep systems secure and compliant. StorageGuard scans customer environments to ensure they are secure and follow all relevant vendor, industry and regulatory best practices.
StorageGuard enables Dell customers to have complete visibility of all security misconfigurations and vulnerabilities in their storage and data protection environment, while hardening these critical systems and guaranteeing compliance with security regulations and industry standards.
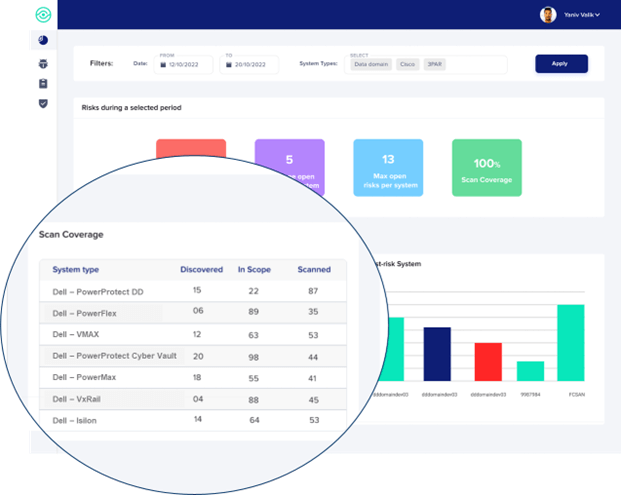
In addition to detecting and remediating security risks across Dell’s storage and data protection systems, StorageGuard also validates configuration and best practices for Dell PowerProtect Cyber Recovery Vault for isolated recovery, ensuring it is air-gapped, isolated, and hardened.
The ETC Program underscores Dell’s commitment to offer customers flexibility and choice with complimentary solutions such as StorageGuard for protecting their critical systems from cyberattacks and insider threats.
“Being invited into Dell’s ETC program is a great honor,” said Gil Hecht, CEO of Continuity. “It also testifies to the powerful value proposition StorageGuard delivers — the ability for Dell customers to assess their vulnerability to cyberattacks and get visibility of security risks across their storage and data protection environments.”
StorageGuard improves the ransomware-readiness and overall security posture of storage and data protection environments. The solution reduces the effort required by ops teams and admins to develop and enforce security policies, prove compliance for audit, and chase down false positive CVE alerts raised by tools that aren’t storage-aware.
[1] Gartner: ‘Innovation Insight for Cyberstorage Solutions to Protect Unstructured Data Against Ransomware’, 8 October 2021
Talk To An Expert
It’s time to automate the secure configuration of your storage & backup systems.