Top 8 Most Common Storage Misconfigurations And Vulnerabilities
About Continuity™
StorageGuard - by Continuity™ - is the ONLY Security Posture Management solution for Storage & Backups, helping to ensure these systems are securely configured, and compliant with industry & security standards.
Introduction
We analyzed data from a large number of storage risk assessments, to provide a unique insight into the state of storage security. The analyzed data covers multiple storage vendors and models, including Dell EMC, IBM, Hitachi Data Systems, HPE, Cisco, Brocade, NetApp, and others.
The analysis covered the configuration of block, object and IP storage systems, SAN / NAS, storage management servers, storage appliances, virtual SAN, storage network switches, data protection appliances, storage virtualization systems and other storage devices.
We discovered over 6,000 security misconfigurations, allowing us to uncover recurring patterns and important security considerations many organizations fail to get right when managing storage & backup systems.
These misconfigurations fit into four main categories:
- Violations of storage vendor security configuration guidelines
- Violation of compliance framework requirements (CIS, NIST, PCI DSS and others)
- Identified storage Common Vulnerabilities and Exposures (CVEs)
- Deviation from community-driven best practices (gathered and generalized from dozens of enterprise internal security baselines for storage – representing shared community insights)
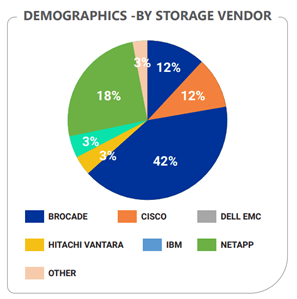
Results
423 enterprise storage devices were analyzed, and a total of 6,300 security risks (vulnerabilities & security misconfigurations) were detected, spanning more than 170 security principles that weren’t adequately followed.
In this post, we address the most common types of security risks found:
- Use of storage vulnerable protocols or protocol settings
- Unaddressed storage CVEs
- Storage access rights issues (over exposure)
- Insecure user management and authentication
- Insufficient or incorrect logging
Three additional risk types were discovered. Although these are less frequent than the top five risks above, each could lead to substantial data compromise if exploited. These include:
- Incorrect use of ransomware-protection features
- Undocumented and insecure API / CLI
- Storage vulnerabilities and oversight in storage software supply-chain management
Lets go through each of the risks, and explain they’re so critical
1. Use of storage vulnerable protocols or protocol settings
Storage protocols span both traditional networking[1] (IP over Ethernet and WAN) and dedicated Fibre-Channel storage networking[2]. It is critical to secure those protocols both during session establishment, and while exchanging data. However, in a far too-high number of cases, and in most environments, it is still common to find configuration gaps such as:
- Not disabling legacy versions of storage protocols, or even worse, defaulting to their use (e.g., SMBv1, NFSv3)
- Use of no-longer recommended cypher suites (e.g., allowing TLS 1.0 and 1.1, not disabling SSL 2.0 and 3.0) – some of which must be disabled to comply with regulatory frameworks (e.g., PCI DSS)
- Not enforcing data encryption for critical data feeds (e.g., management transport, replication transport, backup transport)
- And many others (Allowing cleartext HTTP sessions, using unsecure SNMP community strings, etc.)
| Significance of the risk: cybercriminals can use such configuration mistakes to retrieve configuration information and stored data, and in many cases, can also tamper with (e.g., modify, destroy, lock) the data itself, including the copies used to protect the data. |
2. Unaddressed storage CVEs
There is a variety of software components used for Storage devices, and storage networking, that get updated from time to time, including:
- Device Operating systems (Proprietary, or highly specialized and restricted versions of commercial or open-source operating systems) – for storage arrays and network switches
- Controller firmware
- Management software suites
- API servers (e.g., storage connectors for virtual environments)
Vulnerabilities are discovered on an ongoing basis for such devices, and Common Vulnerability and Exposure (CVE) records are accordingly published. In most cases, a fix in the form of an upgrade, or configuration change is suggested. Common vulnerability management tools used by organizations and enterprises do not detect many storage CVEs (but rather focus on server OS, traditional network gear, software products), and there’s a rather large percentage of storage devices (close to 20%) that are exposed. More than 70 different CVEs were detected in the environments covered in this research (of course, many more exist)
| Significance of the risk: each CVEs details the possible exposures and outcomes it presents – and these span a rather wide range. Among the risks identified in environments that were included in this research were the ability to exfiltrate files, initiate denial-of-service attacks, and even take ownership of files and block devices. |
3. Storage access rights issues (over-exposure)
Access control to storage, includes several different configuration levels:
- Access to storage elements – such as block devices, network shares, or even individual files and objects should be mapped only to designated components (e.g., individual hots or applications). This is done both at the device level (e.g., share configuration, LUN mapping) and using network filtering techniques (e.g., IP filters, SAN zoning and Masking)
- Level of access to the data itself (e.g., read, write, modify permissions and ownership, ACLs)
- Access to advanced storage capabilities (e.g., management, control, replication, snapshot management)
A large number of devices were affected by improper configuration, including unrestricted access to shared storage, unrecommended zoning and masking configuration, ability to reach storage elements from external networks, and more.
| Significance of the risk: incorrect access right management, can at best lead to data exposure, and at worst to compromise of the data itself and its copies, and in some cases, of the operating systems of the hosts that use the storage |
4. Insecure user management and authentication
Storage devices are managed using users and roles, and in many cases, access to the data itself is also regulated using similar means. There are basic recommendations for user management and authentication that are, for a variety of reasons, not kept for storage devices at the same rigor allied for compute and network elements. These include:
- Unrecommended use of local users (as opposed to approved central user management protocols) for routine operations – in far too many cases, default factory accounts were still in use
- Use of non-individual admin accounts
- Not enforcing session management restrictions
- Improper separation of duties (e.g., same roles used to manage data and it’s protection mechanisms – such as snapshots and backups)
| Significance of the risk: incorrect and insecure configuration can allow cybercriminals to take full control over the storage device, up to, and including exfiltration and destruction of the data and its copies. |
5. Insufficient or incorrect logging and auditing
Logging and auditing is a fundamental requirement of any sound security practice – including storge. All administrative activities and security configuration should be logged, and for sensitive information, it is also recommended that storage access should also be logged. Proper logging involves the correct configuration of logging (including level of detail, event types) – the configuration of approved, redundant central logging servers, correct timekeeping and more. A large percentage of production storage devices (around 15%) were not logged at all, and a substantial additional percentage of those that were logged was susceptible to manipulation.
| Significance of the risk: improper logging can help cybercriminals mask malicious activities, and interfere with the ability of central security tools to detect anomalies. |
6. Incorrect use of ransomware-protection features
Modern storage devices become more sophisticated, and offer advanced ransomware detection and prevention capabilities, as well as advanced capabilities for locking retained copies, protecting critical data from tampering and deletion, and certain forms of air-gapping. These features are often overlooked – and even when used, many configurations did not meet vendor best-practices.
| Significance of the risk: limited or no protection from ransomware, cybercriminals can easily circumvent or disable protection mechanisms. |
7. Undocumented and insecure API / CLI
There is a surprising number of ways storage devices can be manipulated and managed:
- Using device APIs
- Using management hosts and API gateways
- In-band – using storage protocols
- Using dedicated host agents
- Using storage agents on virtual infrastructure
Most of those control methods can be further managed to define what access level in can provide (e.g., which actions are allowed -including creation, destruction, mapping, copying, and more), what components could be controlled, filtering as to which IPs, devices and objects can connect and more.
It is of an utmost importance to approve and document all allowed connections, limit their access level and scope to the minimum, and to actively block any other connection.
In around 10% of the environments (!) undocumented API entry points were found, whose purpose could not be accounted for, and in around 20% of the environment approved mechanisms were not properly hardened and limited.
| Significance of the risk: undocumented and insecure API and CLI access paths can provide a cybercriminal with a backdoor to control storage devices, exfiltrate data, and tamper with storage content and its backups. |
8. Storage vulnerabilities and oversight in storage software supply-chain management
As already discussed, storage device updates are regularly issued. In certain organizations these updates, as well as transfer of support information is performed with designated vendor support environments outside of the customer premises. In other organizations, even though it’s an established policy to not allow connection to vendor support environments – such connections were still found enabled and active.
In any case, there’s a set of minimal safeguards that need to be observed in regards to software updates (manual or automated) – including proper signing, proper end-to-end encryption when obtaining binaries, proper authentication and IP filtering, etc.
In several of the environments, configuration issues were detected that can allow unapproved images to be deployed, or can allow a cybercriminal to intercept and tamper with data transfer and support sessions.
| Significance of the risk: improper control and enforcement of software supply-chain paths can allow cybercriminals to tamper with the storage OS, and thereby gain full control over the devices, the data, and its protective copies. |
StorageGuard helps to securely configure your storage, backup and data protection systems. It runs an automatic configuration audit to ensure you’re meeting your configuration baseline, while detecting and resolving configuration drifts.
There are great resources and tools out there, to help you identify and remediate storage & backup security risks.
One good place to start is The State of Storage Security Report. Click here to download the report.
The Industry-First Research – The State of Storage Security
Continuity has published a new research report that provides an analysis of the vulnerabilities and misconfigurations of enterprise storage systems.

Talk To An Expert
It’s time to automate the secure configuration of your storage & backup systems.