
The most critical – and overlooked – security issues facing financial services
About Continuity™
StorageGuard - by Continuity™ - is the ONLY Security Posture Management solution for Storage & Backups, helping to ensure these systems are securely configured, and compliant with industry & security standards.
A few words about the author: John Meakin is a seasoned and experienced CISO with more than 30 years of experience in various financial services companies, such as RBS, Standard Chartered, and Deutsche Bank. He is also a member of our advisory board.
Data is a major part of the role of any CISO. When it comes to the financial services industry, data is even more important and valuable than in many other industries – both customers’ private data and critical financial data. Securing storage and backup systems isn’t always obvious and isn’t always the focus of many CISOs or their teams. I admit that it wasn’t part of my focus until quite recently.
So, what is the big picture of storage and backup security? Is this a Cinderella area in the pursuit of real security focus? How can you prepare? And where do you go from here? I will share with you my views in this article.
All eyes on storage and backup
It’s no secret that modern security is focused on data, particularly in the financial services industry. The rise – and sophistication – of ransomware attacks that compromise data most of all has been well documented.
From industry publications like Threatpost…
“Cybercriminals behind a string of high-profile ransomware attacks, including one extorting $11 million from JBS Foods last month, have ported their malware code to the Linux operating system.”
…to analysts like Gartner…
“Harden the components of enterprise backup and recovery infrastructure against attacks by routinely examining backup application, storage and network access and comparing this against expected or baseline activity.”
…to governments finally addressing the issue, like in this recent White House memo:
“Test the security of your systems and your ability to defend against a sophisticated attack.”
Ransomware IS focused on data. As such, the key to mitigating (and ideally neutralizing) that threat is to secure data in storage and backup.
20 years ago we thought of data in terms of files on disk, or perhaps even tape-based systems. Data storage and backup infrastructure is very different today, with most data stored online for instant and flexible access, and malicious actors know it. Unfortunately, even with the exponential rise in ransomware attacks, the protection of storage and backup systems isn’t as much of a focus as it should be within security circles.
We tend to think of backups as the final layer of protection against ransomware, though in reality, they are simply another repository of data in storage, ready to be harvested if not appropriately secured. And, critically, these days most backups are stored on-line in the instant-on world.
This begs the question: are we as CISOs and security leaders currently focused on one of the most pressing risks?
The unspoken gap
The value of business data is growing annually in virtually every organization. As businesses want to optimize their business models through analytics and a better understanding of customers, even older data is of great value. And of course, all our customers value their own data that they have entrusted to our businesses. Malicious actors recognize this fact, so data-centered attacks continue to grow both in number and sophistication.
Are we really rising to this challenge as CISOs and security leaders? Have we spent enough time analyzing and reinforcing those darker parts of our storage infrastructure that any smart threat would target? This industry-wide oversight is exactly why so many of these attacks succeed.
Perhaps the more compelling proof, beyond the flashy headlines mentioned above, lies in the cyber insurance market. Larger insurers are beginning to pull out because it’s not good business – there are simply too many claims for ransomware and data-theft attacks to cover!
When ransoms are paid – and in 20% of cases, they are – it indicates that victims have completely lost access to their data, including backups. Meanwhile, these payments only serve to encourage and embolden the bad actors.
There are other myths that many CISOs and security leaders believe – covered in detail in this blog and whitepaper – which feed the current exponential growth of attacks and further demonstrate the industry’s continued failure to focus on storage systems. They are the greatest current oversight in security.
The shift in voice and focus of the financial services CISO
The truth? In a cloud-fuelled world, storage layers deserve as much attention as computing and networking layers. Cloud providers offer cloud storage as a separate service, carrying a separate set of controls and risks – access keys in AWS S3 storage, for example.
Storage security issues aren’t limited to the cloud either; they spread across the full spectrum of hybrid and on-premise infrastructures. And storage systems have increasingly become separate systems with their own compute and management platform, whether they are on-prem or in-Cloud. All these modes of storage constitute separate systems, but for whatever reason, they haven’t enjoyed the same attention from infrastructure and security experts as those on other layers.
The need for change is also reflected in this recent Security Intelligence Report conducted amongst financial services security professionals:
- Two-thirds believe that a storage attack will have ‘significant’ or ‘catastrophic’ impacts.
- 60% are not confident in their ability to recover from a ransomware attack.
- Two-thirds say securing backups and storage was addressed in recent external audits.
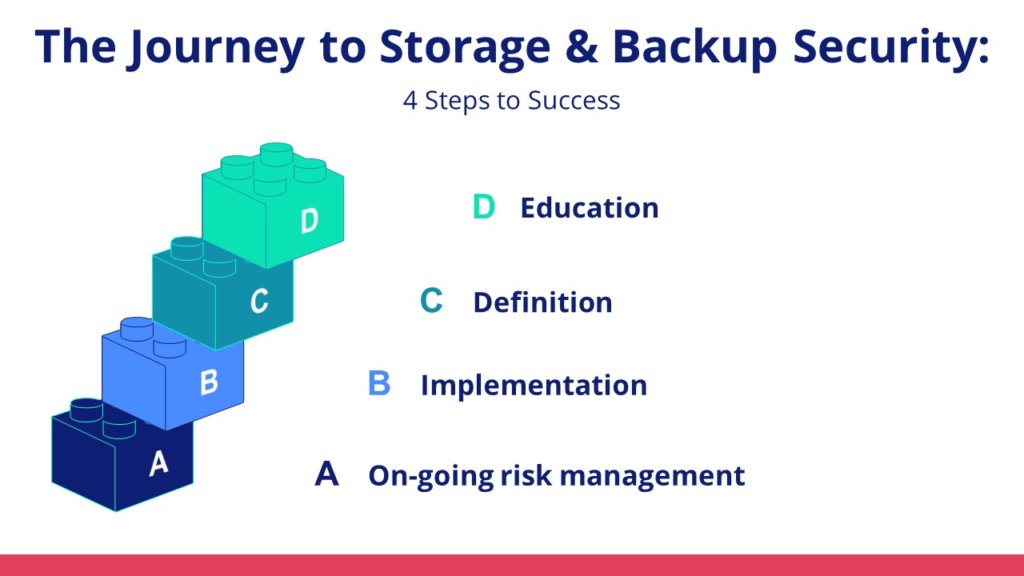
Heading for a better future… but how? 4 steps for success
Now that we understand the problem, what’s the solution?
Many CISOs already follow the steps below when faced with a new threat. While we’re not here to deliver a tutorial on how to teach a fisherman how to fish, it’s nonetheless critical to revisit the fundamentals to ensure we’re covering the increasing storage security problem in the correct and thorough way it deserves. At this point, we’re playing a game of catch-up and can ill-afford missteps.
Use the following four steps to form the foundation of your storage and backup security approach:
Education
The first step is to understand the capabilities of your storage and backup devices. In your real environment, what do you have (not just in theory): which vendors do you use, how are their technologies deployed, and how are roles and responsibilities defined?
With lots of storage platforms in widespread use, there can be a lack of understanding as to the technical details of how each works. Ask yourself:
- What should I know?
- What don’t I know?
- What’s my technology landscape?
- What are my storage strengths and weaknesses?
An excellent place to begin in this phase is to perform an initial assessment of your storage and backup security. This assessment will detail any risks identified and include the corrective steps for remediation.
This recent security guide published by NIST (co-authored by Continuity) is an excellent resource for those looking to develop their storage infrastructure knowledge. It provides a thorough overview of current storage technologies and their relative risk landscapes.
Definition
Once you get the lay of the land, you should define ‘secure enough’ baselines of your storage and backup environments. They need to be detailed since these environments are complex and the attack surface is multi-faceted.
For instance: what kind of roles are needed? What kind of controls do we want to have? What level of auditing do we expect?
Once you define these baselines, it’s much easier for the storage and backup managers to make sure they’re fully implemented, audited, and monitored
We also need to define threats and robust security protocols.
So, you should aspire to:
- Analyze relevant threats and risks.
- Document requirements and security baselines.
- Establish procedures.
Implementation
With knowledge accrued and threats defined, the rubber needs to hit the road. Now comes the stage of implementing the controls that were previously defined. Please note: usually when the initial gap analysis is done (remember step 1), you end up with a long list of deviations. Now’s the time to iron them out.
Implementing automation in performing these changes is key to making sure the control wrap to the attack surface closely.
Another practice I recommend here is to build KPIs and automatic measurements for the predefined baselines, in order to make sure they are always met.
So, in essence, at this stage security leaders must:
- Harden storage
- Implement controls
Ongoing risk management
Storage and backup security demands active, ongoing risk management. As threats continue to evolve, so must we. In order to keep up, lean on:
- Measurement
- Reporting
- Automation
While the above steps might seem obvious until now their implementation within the area of storage and backup has been less so. Security leaders need to be in dialogue with the infrastructure teams to ensure that this set of risks is being taken as seriously as it needs to be.
Reaching a common agreement that there’s a problem that needs to be solved is perhaps the most important step of the entire process.
Throughout every step of this journey, you can use your trusted storage vendors to help ensure that you’ve done things correctly.
When you build enough automation you not only enjoy a much more secure environment, but you also have the opportunity to present to auditors the actual state of your storage and backup environment much more easily, using the measurements that automation makes available. Without automation, it will be a possible, but tedious, task.
The journey to storage and backup security used to take several months to deploy. But nowadays it can be completed in a few weeks, even in large environments.
In conclusion
Data is the bread and butter of the 21st century. And just as these valuable resources have always needed to be securely stored and protected, in the digitized, data-everywhere world, an organization must make significant investments in data protection, and storage and backup hardening. CISOs have the skill to do it; many simply lack a clear view of the problem. The problem needs to be reframed in the minds of security experts, and fast, as ransomware is already beginning to become a runaway train.
Where to start? Perhaps with an evaluation of your current storage and backup cyber-resiliency. In this questionnaire, you’ll be asked nine simple questions, before being given a score based on your resilience, as well as a personalized set of recommendations that light the path forward.
Talk To An Expert
It’s time to automate the secure configuration of your storage & backup systems.