Five Levels of Configuration Baselines: A Roadmap to Hardening Your Storage & Backup Systems
About Continuity™
StorageGuard - by Continuity™ - is the ONLY Security Posture Management solution for Storage & Backups, helping to ensure these systems are securely configured, and compliant with industry & security standards.
In today’s complex enterprise environments, maintaining consistent and secure configurations across heterogeneous systems is no easy feat. From storage arrays and backup software to cloud repositories and SAN fabrics, every system must adhere to well-defined configuration standards to ensure resilience, compliance, and cyber readiness.
That’s where configuration baselines come in.
Why Configuration Baselines Matter
A configuration baseline defines the expected settings and controls that every system should follow. Much like a checklist for secure and reliable operations, baselines ensure that all systems are configured according to best practices and organizational requirements.
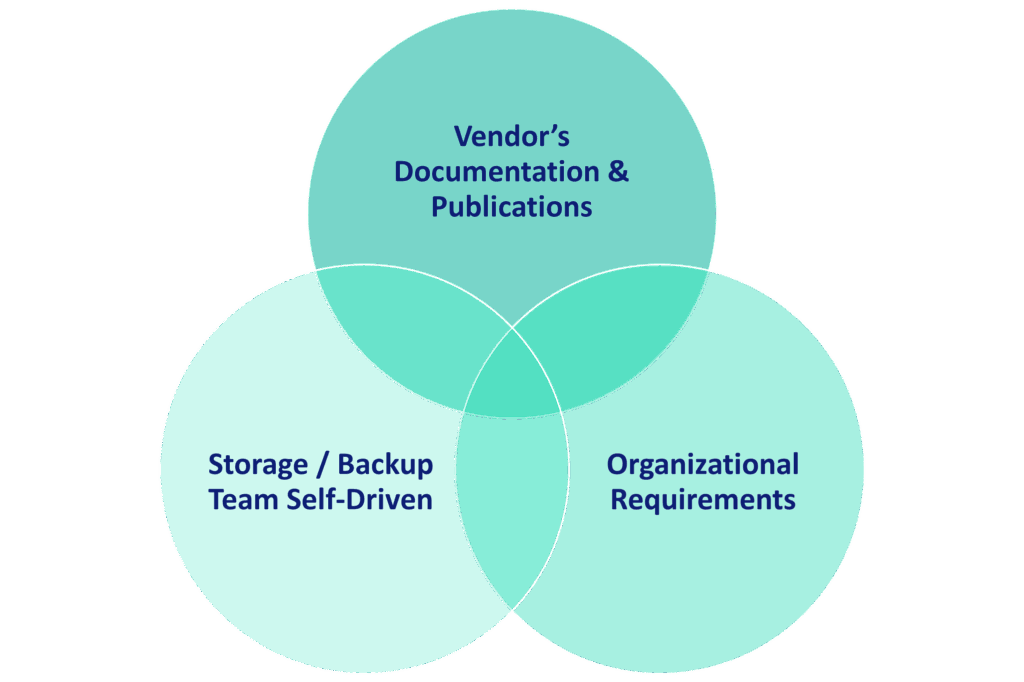
When properly implemented, configuration baselines:
- Help maintain hardened, healthy, and resilient systems
- Enable compliance with internal and external standards
- Simplify audit preparation and risk management
- Provide a foundation for continuous security improvement
For example, a simple but crucial baseline requirement is to configure Network Time Protocol (NTP) for accurate time synchronization across systems – essential for logging, auditing, and correlation.
The Anatomy of a Baseline Requirement
Each baseline requirement should be clearly documented and traceable. A well-structured baseline entry typically includes:
- Summary – A short description of the control (e.g., “Disable Telnet access”)
- Rationale – Why this control is needed and what risk it mitigates
- Product-specific details – Relevant models, versions, and implementation notes
- Lifecycle data – Creation, review, and update dates
- References – Vendor or regulatory sources
This approach allows teams to build, verify, and maintain baselines in a repeatable and scalable way.
The Tiered Baseline Approach: Gradual, Measurable Improvement
Not all systems are equally sensitive — and not every organization can jump straight to “perfect” hardening. That’s why tiered, progressive baselines provide a practical path for continuous improvement.
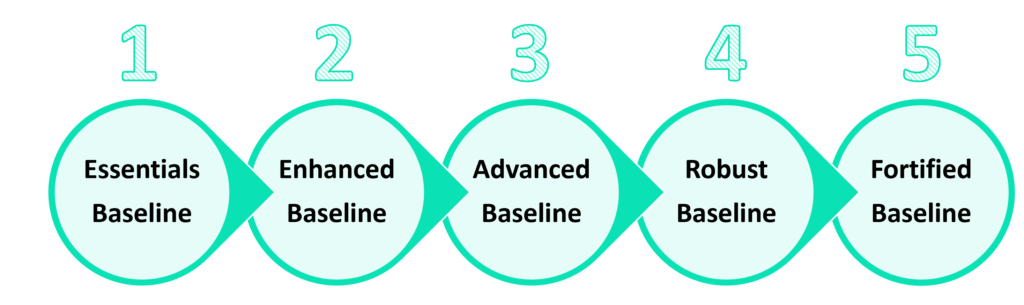
Each tier represents a progressive level of configuration maturity:
Level 1: Essentials
Focus on foundational controls like:
- Disabling Telnet and insecure protocols
- Enforcing password policies
- Enabling multifactor authentication
- Setting role-based access controls (RBAC)
- Denying default Fibre Channel zones
Level 2: Enhanced
Build on essentials by adding:
- IP Access Control Lists (ACLs)
- Remote support and email alert configurations
- NTP and system time settings
- Encrypted data-at-rest where applicable
Level 3: Advanced
Strengthen your security posture with:
- Valid certificate enforcement
- Secure SNMPv3 configurations
- Syslog integration and strong cipher suites
- Dual authorization for destructive operations
- Encryption for backup traffic
Level 4: Robust
Push towards resilience with:
- No root login
- Internal firewall enforcement
- SMB signing and NFSv4 + Kerberos
- Anomaly detection and authorized server lists
- Segregated management and data networks
Level 5: Fortified
Achieve full hardening and audit readiness with:
- External key management
- FIPS mode enforcement
- Secure syslog and time synchronization
- Smart card (PIV/CAC) authentication
- Cloud/SaaS connection restrictions
This tiered methodology allows enterprises to customize their journey – defining their starting point and target maturity by system criticality and sensitivity.
Common Enemies of Configuration Baselines
Despite best intentions, many organizations struggle to maintain consistent baselines due to:
- Heterogeneous environments spanning multiple vendors and products
- Frequent provisioning/decommissioning cycles
- Mergers & acquisitions, introducing configuration drift
- Manual verification processes that can’t scale
- API/CLI changes introduced by vendors
- Outdated baselines not reflecting new threats or compliance updates
To combat these, periodic reviews and automation are non-negotiable.
Keeping Baselines Current: Continuous Verification
A baseline is only as strong as its maintenance process. Organizations must routinely assess whether:
- New features or CLI/API changes affect baseline implementation
- Updated vendor best practices or security advisories exist
- New audit or compliance requirements have emerged
- Internal policies have evolved
This requires continuous research, verification and configuration drift detection, ideally through automated tools.
How StorageGuard Helps
StorageGuard simplifies baseline management for enterprise storage and backup systems by providing:
- A built-in risk library of best practice configuration checks
- Automated scans (scheduled or on-demand) for drift detection
- Secure configuration and hardening guidelines mapped to NIST, CIS, ISO, PCI DSS, HIPAA, and STIG standards, etc.
- Integration with ITSM, SIEM, and dashboarding tools
- Single control plane for heterogeneous storage and backup environments (Dell, NetApp, Hitachi Vantara, HPE, Pure, IBM, Rubrik, Commvault, Cohesity, Veeam, Veritas, etc.)
With StorageGuard, teams can configure, verify, and enforce baselines across all storage and backup assets — reducing the attack surface and strengthening overall cyber resilience.
Key Takeaways
- Use tiered baselines for a practical, progressive hardening approach
- Keep your baselines current and aligned with cyber threats, vendor and compliance guidelines
- Automate detection and remediation of deviations
- Embrace continuous verification to maintain confidence in your security posture
Automation is key – because in complex enterprise storage and backup environments, manual compliance is no longer sustainable.
Ready to start building your baseline?
Learn more about how StorageGuard can help you strengthen your storage and backup environments.
Talk To An Expert
It’s time to automate the secure configuration of your storage & backup systems.