CISO Point of View: Discover how other CISOs deal with the complexity of data protection and storage security
About Continuity™
StorageGuard - by Continuity™ - is the ONLY Security Posture Management solution for Storage & Backups, helping to ensure these systems are securely configured, and compliant with industry & security standards.
Data plays an increasingly important role in the modern enterprise. With digitization, data comes much closer to the customer – with large amounts of data being captured to streamline services.
As data becomes more valuable, it becomes a key piece – if not the primary piece – of intellectual property of any organization.
The other side of the coin is that attacks on data pose the greatest threat to organizations. A dramatic shift has occurred in the cyber threat landscape in recent years, with the exploitation of organizational data being a prime target for cyber criminals.
As data-targeted attacks increase in sophistication and number, cybercrime grows nearly exponentially. According to Cognyte CTI Research Group, ransomware attacks alone nearly doubled in the first half of 2021. More specifically: 1,097 organizations in 66 countries throughout 18 industry verticals were hit by ransomware attacks in the first half of 2021.
As with any other fast-growing industry, cybercrime will also likely see significant reinvestment of profits and increased innovation. In other words, we can expect things to get worse as new forms of data-targeted attacks emerge. In fact, Cybersecurity Ventures predicts cybercrime will cost the world in excess of $6 trillion annually by 2021, up from $3 trillion in 2015.
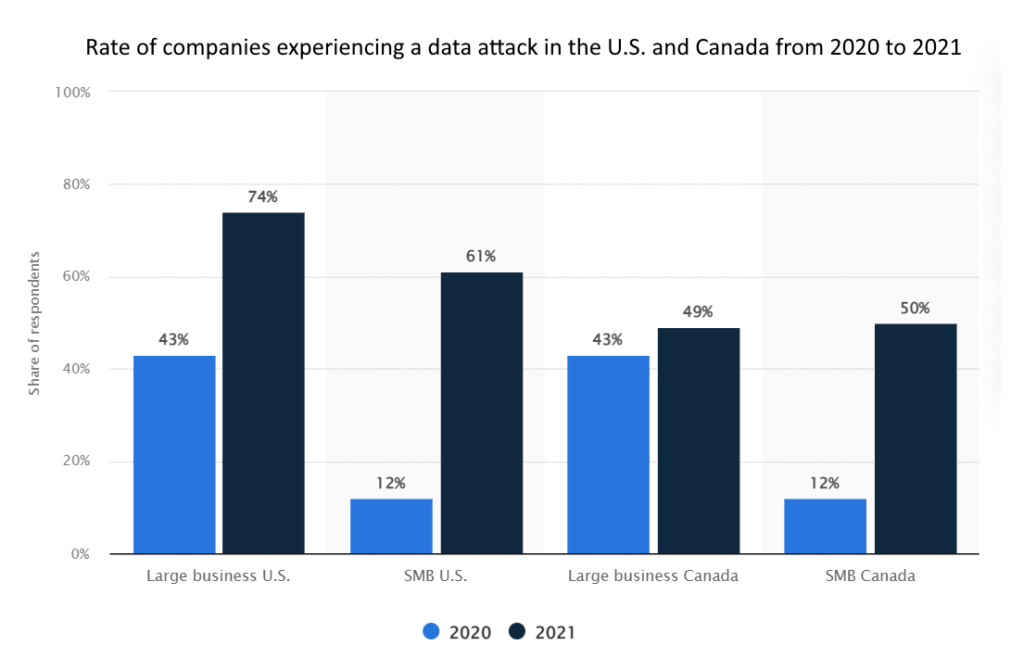
In this gloomy environment, regulators cannot sit idle and must now pay much closer attention to the organization’s responsibility to ensure the integrity, resilience, and recoverability of their data.
Changes in the way we secure data
With the increased value of data, new security challenges arise. One such concern is unchecked growth, which is sometimes reflected by the misalignment of the tech side, security side, and compliance side of the same organization. Take this example: The infosec team may have been copying one server’s shares to another server’s shares, amassing a huge amount of data that, while of little use to the organization, may in fact be considered sensitive data from a compliance standpoint.
It can be difficult to predict which data sets are valuable and which are not. Does that mean all data must be considered valuable until exhaustively ruled out?
Ensuring data security is another common concern. Not only because regulations and standards are more stringent, but because we need to keep customer data accurate and secure in order to build a lasting relationship.
Finally, as the value of data is recognized across the organization, a growing number of stakeholders launch independent data analysis initiatives. As a result, controlling who has access to the data and what level of access is granted, becomes extremely challenging.
How cyber-related technology adapts to this new reality?
There are mixed feelings about how well technologies have adapted to meet the increase in the business value of data. Some CISOs feel that advances in data management solutions will stay ahead of data growth, primarily through the evolution of the cloud.
However, there are some concerns voiced amongst CISOs about lack of technology maturity and scalability to solve these data security challenges:
- Data Loss Prevention (DLP) is widely considered an immature, or even an unfulfilled promise.
- Lack of visibility and security blindspots.
- Ransomware is becoming more sophisticated, and an almost routine occurrence.
- Companies rely on third parties for their digital transformation journey; however, third party security risks often don’t get the attention they require.
- Too little focus is paid to data recoverability.
So, have we reached the point where security practices need a serious overhaul? Are we doing enough? And putting data protection aside for a minute; what steps should organizations take to harden their storage and backup systems?
A wide industry effort to improve control over storage and backup environments is surely possible with better guidance from vendors. A recent focus on improving knowledge sharing and awareness of storage security best practices is definitely a good sign that the industry is moving in the right direction. NIST SP-00-160, for instance, provides guidelines for architecting cyber resilience, and NIST SP-800-209 provides detailed guidance on securing backup and storage systems.
In addition to NIST, Gartner also published a report in October 2021 entitled “Innovation insight for cybersecurity solutions to protect unstructured data from ransomware”. The report notes that “I&O leaders must evaluate cyber storage solutions as a new defense mechanism to protect their most critical data.”
The CISO perspective – written by CISOs for CISOs
We asked CISOs about the subject of securing data assets:
- What contributes to the increase in the business value of data?
- In what ways is technology adapting to this change?
- Which security practices have evolved and do they align with the current business needs?
- CISOs lessons learned: how have you approached data protection throughout your career? What went well and what didn’t, and what would you have done differently?
- To take a risk-based approach to data protection and recovery, where should other CISOs begin?
We interviewed these eight seasoned CISOs and cybersecurity leaders to get their unique insights and their top recommendations for their peers. Spoiler alert: Focus on better policies, and better design are key elements.

Here’s a sneak preview before we leave
Gaining insights from experienced CISOs in different industries and disciplines is always very valuable. Clearly, data is valued, and data-targeted attacks are a concern across all levels of organization leadership. With no realistic way to completely bulletproof an organization, it has become apparent that the backup and storage services truly are the last line of defense.
The participating CISOs were united in several key concerns:
- Technology is not evolving fast enough. Many capabilities adapt, but at too slow a pace, while storage infrastructure security remains a hit-and-miss affair. There are certain innovations (e.g., immutable storage, offsite cloud archives, threat intelligence), but they tend to be discrete capabilities that do not blend together well.
- Information security practitioners lack visibility and control over the security posture of storage and backup planes. Infrastructure and security teams don’t share the same security vision – and sometimes even contradict it.
- There is much room for improvement throughout the data management lifecycle. Improved classification, clear and detailed definition of security baselines, visibility, and governance.
This is the gist of it. CISOs share more insights and recommendations in the full guide (it’s free).
Talk To An Expert
It’s time to automate the secure configuration of your storage & backup systems.