6 Things Financial Services CISOs Should Do To Prepare For The New Digital Operational Resilience Act (DORA)
About Continuity™
StorageGuard - by Continuity™ - is the ONLY Security Posture Management solution for Storage & Backups, helping to ensure these systems are securely configured, and compliant with industry & security standards.
A few words about the author: John Meakin is a seasoned CISO with more than 30 years of experience in various financial services companies, such as RBS, Standard Chartered, and Deutsche Bank. He is also a member of Continuity’s advisory board.
It’s no secret that modern security is focused on data, particularly in the financial services industry. The rise – and sophistication – of ransomware attacks has been well documented – and these almost always focus on data, either for theft or destruction, or both. The most recent wave are attacks on storage and backups:

- “The Conti ransomware gang has developed novel tactics to demolish backups…. “It’s one of the most ruthless of the dozens of ransomware gangs that we follow.” [ThreatPost]
- “The ransomware was targeting poorly protected Network-Attached Storage (NAS) devices. The threat actors exploited known vulnerabilities.” [Security Affairs]
- “This new ransomware gang is known to seek out and delete any backups to prevent them from being used by the victim to recover their data.” [Bleeping Computer]
It’s for this reason that many regulatory bodies and industry standards are now taking a much closer look at the security of storage & backup systems:
- “Periodically and proactively assess configuration compliance to storage security policy.”
[NIST Special Publication 800-209; Security Guidelines for Storage Infrastructure]
- “Control Backup copies of information, software and systems shall be maintained and regularly tested in accordance with the agreed topic-specific policy on backup.”
[ISO/IEC 27001; Information Security Management Systems]
- “Actively manage the security posture of the storage technology and protection mechanisms… Perform regular security threat assessments to evaluate security readiness… All operating systems, hypervisors and applications should be hardened relative to the use of the storage system.”
[ISO 27040; Information Technology Security Techniques: Storage Security – to be published at the end of 2023]
- “Maintain an up-to-date inventory of networked assets…, identify software vulnerabilities, track how often the agency enumerates its assets, how current its vulnerability signatures are; and provide asset and vulnerability information to CISA’s CDM Federal Dashboard. This Directive applies to central storage devices (For example SAN, NAS, backup appliances). In addition to discovery scanning, storage devices should at minimum support a subset of vulnerability enumeration.”
[Cybersecurity and Infrastructure Security Agency (CISA) – Binding Operational Directive 23-01]
The need for change is also reflected in the research report Analysis of Storage & Backup Security in the Financial Services Sector, which highlights that:
- Two-thirds of respondents believe that a storage attack will have a ‘significant’ or ‘catastrophic’ impact;
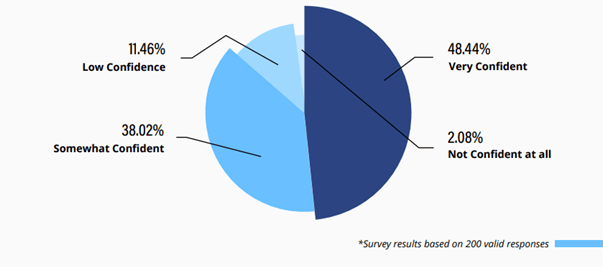
- 60% of them lack confidence in their ability to recover from a ransomware attack; and
- Two-thirds say securing backups and storage was a focus of recent external audits.
Various industry and government regulators have woken upto the serious systemic threats from cyber insecurity. The latest regulation to enter the scene in Europe is the Digital Operational Resilience Act (Regulation (EU) 2022/2554) – also known as DORA.
DORA will have a significant impact on the way financial institutions secure data storage and backup systems. The framework requires financial institutions to have a robust and resilient storage and backup system in place to protect their data from unauthorized access, loss, or corruption. Without their data, preserved and secure, regulators know that businesses cannot be resilient faced with the current threat environment.
Specifically, with regard to data storage and backup, DORA requires financial institutions to:
- Have a documented data retention policy that specifies how long data should be stored and how it should be disposed of
- Implement appropriate technical and organizational measures to protect data storage and backup systems from unauthorized access, loss, or corruption of data
- Test and monitor their data storage and backup systems on a regular basis to ensure that they are working properly
- Ensure that data is protected from risks arising fduring its processing,, including poor administration, processing related risks and human error
- Ensure backup systems don’t jeopardise the security of the network and information systems
Therefore, to ensure compliance with DORA and to get ahead of the regulators, CISOs should take the following 6 steps to ensure that their storage and backup systems are secure and resilient:
- Review current data storage and backup policies and procedures to ensure that they meet the requirements of DORA.
- Build up knowledge and skill sets – and improve collaboration between Infosec and IT infrastructure teams. If you don’t know where your data is stored and backed up, or you are not clear on responsibility for keeping it secure, you cannot be resilient.
- Define comprehensive secure baselines for all storage and backup infrastructure components.
- Use automation of configuration, control and vulnerability management of storage and backup infrastructure to reduce exposure to risk, and allow much more agility in adapting to changing priorities and threats,
- Apply robust controls and comprehensive testing of storage and backup security and test your ability to recover from an attack. This will not only improve confidence, but will also help identify key data assets that might not yet have the required level of protection.
- Ensure that your approach includes all aspects of storage and backup management, including often-overlooked key components such as Fibre-Channel network devices, management consoles, etc.
By taking these steps, CISOs can help to ensure that their businesses are compliant with DORA and that their data is protected from unauthorized access, loss, or corruption. Through this their businesses will be more resilient.
Automating the hardening of storage and backup systems to be resilient
There are a great many patch management and vulnerability management tools out there. They continually scan networks and systems for security risks. They do a fine job with operating systems (OSes) and enterprise applications. However, due to the slightly different architectures – and sometimes unclear responsibilities – they often miss security misconfigurations and vulnerabilities in storage and backup systems.
There are currently thousands of active CVEs out there that relate specifically to storage and backup systems. They can be used by hackers to exfiltrate files, initiate denial-of-service attacks, take ownership of systems, block devices, and delete data. Overall, about 20% of storage and backup devices are exposed and can be attacked successfully by ransomware.
In fact, many organizations fail to configure immutable backups properly, even when the infrastructure provides this important feature – possibly the result of insufficient understanding of the technology and its limitations. This allows adversaries to compromise those backup systems.
One way of avoiding these pitfalls is to deploy a tool that is specifically designed to focus on the storage and backup challenge, and help solve it through automated compliance checks. One such tool is…. StorageGuard which finds the security risks that other vulnerability management tools miss. Developed specifically for storage and backup systems, it runs automated compliance checks to detect thousands of possible security misconfigurations and vulnerabilities at the storage and backup system level that might pose a security threat to enterprises data.
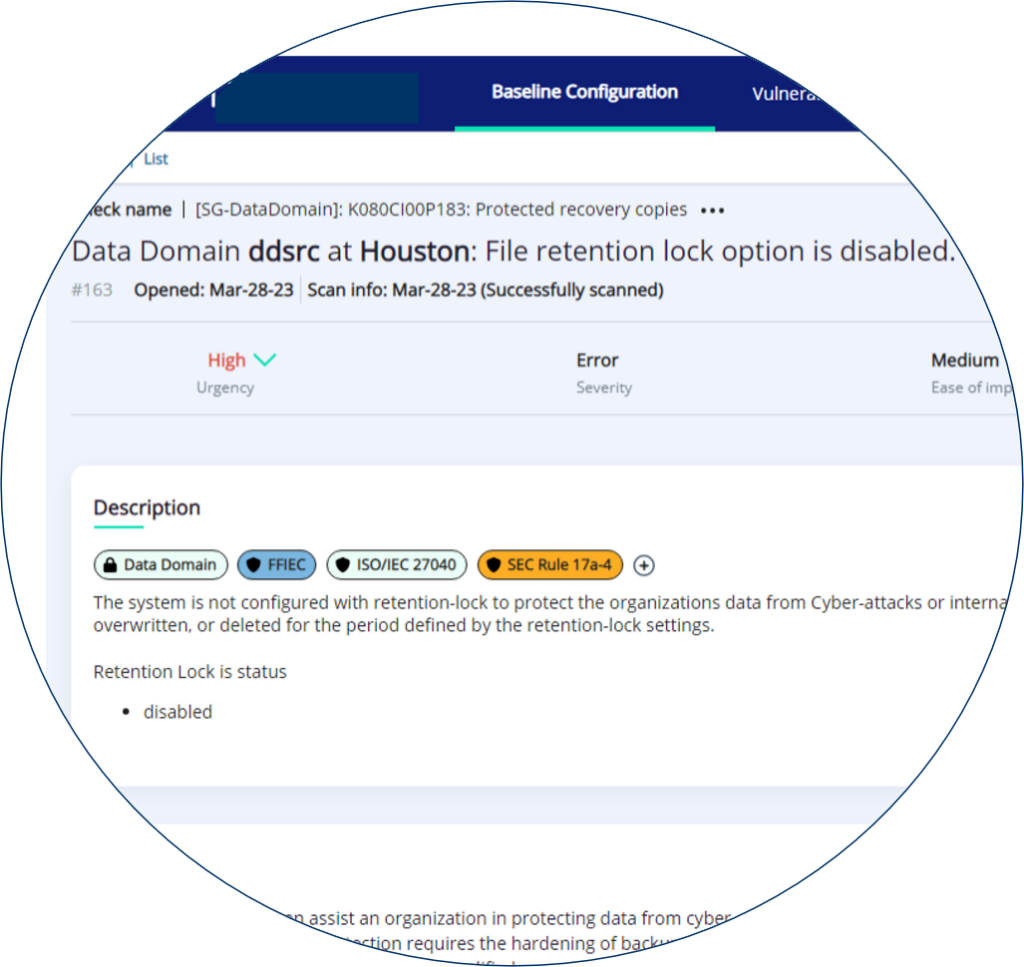
It analyzes block, object, and IP storage systems, SAN/NAS, storage management servers, storage appliances, virtual SAN, storage networking switches, data protection appliances, storage virtualization systems, and backup devices.
StorageGuard ensures these systems will never be the weakest link in cybersecurity. Its comprehensive approach to the scanning of storage and backup systems offers complete visibility into blind spots, automatically prioritizing the most urgent risks, and remediating them.
Talk To An Expert
It’s time to automate the secure configuration of your storage & backup systems.