Our Blog
Stay in-the-know with all things storage & backup security,
vulnerability management, and ransomware protection
Backup Blog Bites #3: The Backup Immutability Do’s & Don’ts Checklist
Since backups are becoming lucrative targets for cybercriminals, vendors like Cohesity, Commvault, Dell, Rubrik, Veeam and Veritas have responded with new ransomware protection features – including immutability.

Storage & Backups Under Attack. This Is What To Do About It
Over the past few months there has been a significant increase in publicized attacks on storage & backup systems, e.g. You can read more about these

Backup Blog Bites #2: To AD Or Not To AD Your Backup System? That Is The Question
When it comes to backups, there’s an interesting debate as to whether you should connect your backup systems to Active Directory (AD) or not, and for

Backup Blog Bites #1: Is Your Immutable Backup Vulnerable to Time Spoofing Attacks?
What this is about? This time-based attack happens when an attacker manipulates insufficiently-secure time sync configuration to trick the backup systems into thinking that “X” number

After The Johnson Controls Ransomware Attack, Here’s An 8-Point Security Checklist For Your Backups
On September 27th, Johnson Controls International announced a massive ransomware attack, that encrypted many of the company devices, including VMware ESXi servers. This impacted the company’s

StorageGuard vs Rapid7 InsightVM: A Comprehensive Comparison
In the world of cybersecurity, staying ahead of threats and vulnerabilities requires a multifaceted approach. Two prominent solutions in this field are StorageGuard and Rapid7 InsightVM. While both tools have distinct focuses, they also complement each other in ways that can significantly enhance an organization’s security posture. In this blog post, we will delve into the key features, benefits, and how these two solutions work together seamlessly.

Validating the Security Posture of Cohesity DataPlatform with StorageGuard
StorageGuard’s security validation checks cover a wide range of system components, access controls, authentication mechanisms, encryption settings, monitoring configurations, and more. These checks are specifically tailored to ensure that Cohesity DataPlatform adheres to industry best practices and security standards.

6 Things Financial Services CISOs Should Do To Prepare For The New Digital Operational Resilience Act (DORA)
To ensure compliance with DORA and to get ahead of the regulators, CISOs should take the following 6 steps to ensure that their storage and backup systems are secure and resilient

Don’t Rely On Immutable Backup For Protection Against Ransomware
StorageGuard plays a critical role in your cyber resiliency strategy, by helping you increase usage & adoption of your existing data protection tools – and subsequently get more out of your current investment.

To Fight Ransomware, We Need to Fill The Cultural Gap
In the past two years, cybercriminals have become increasingly skillful at destroying the organizational backup first, only then locking the data – leaving victims no choice but to pay the ransom. Given how long this trend has been around, and the devastating impact of a successful attack, one would expect organizations would get things under control by now. If anything, the situation is worsening.

Continuity Joins Dell Technologies ETC Program to Help Protect Customers’ Storage and Data Protection Systems
The ETC Program underscores Dell’s commitment to offer customers flexibility and choice with complimentary solutions such as StorageGuard for protecting their critical systems from cyberattacks and insider threats.

Best Practice Guide: Meeting Backup Requirements for Cyber Insurance Coverage
Cyber insurance provides a cushion to fall back on in a successful cyber-attack, providing coverage for damages caused by data loss.

How To Demonstrate Backup Compliance. A Practical Guide
Compliance to industry standards and regulatory mandates can absorb a huge amount of time. Organizations need to verify they comply with the different requirements of security frameworks and regulations such as CIS, NIST, PCI DSS, ISO, and others.

The CISOs Guide to Storage & Backup Cyber Resiliency
CISOs rely on information from across the organization about security, particularly from the various IT departments. Unfortunately, the information being fed to CISOs about the state of cybersecurity risk is incomplete. There is a blind spot present – a gaping hole.

Top 4 Predictions for Storage and Backup Security in 2023
2022 clearly demonstrated that attacks on data represent the greatest cyber-threat organizations face. The attack pace not only continued, it accelerated.

Gartner Promotes the Need for Heightened Storage & Backup Security to Combat Ransomware
Gartner recently emphasized the need for much stricter security in a recent report. Gartner analyst Julia Palmer focused on emerging innovative storage and data protection technologies.

6 Steps to Ensure Compliance For Your Storage & Backup Systems
Here are just a few of the areas that must be considered to ensure thoroughness in verifying backup and storage compliance

The Storage Manager’s Quick-Guide to Ransomware Resiliency (Part 2)
Why storage managers need to prepare for the ransomware scourge?

The Storage Manager’s Quick-Guide to Ransomware Resiliency
Why storage managers need to prepare for the ransomware scourge?

What’s Wrong with Storage and Backup Ransomware Protection Capabilities? (An Overview of Immutability, Snapshots, Air-Gap & Data Recovery)
Storage is becoming a prime target of cybercriminals as they attempt to infiltrate the enterprise. Faced with a wall of perimeter defenses, security safeguards, and well-patched

Five Reasons Why Storage and Backup are Cybersecurity’s Weakest Links
A lot of money is being spent to proof up the enterprise against intrusion. Ransomware protection is currently in the spotlight – and with good reason.
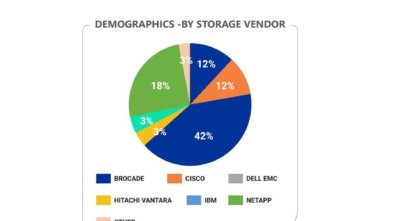
Top 8 Most Common Storage Misconfigurations And Vulnerabilities
Introduction We analyzed data from a large number of storage risk assessments, to provide a unique insight into the state of storage security. The analyzed data

5 Takeaways From The New Gartner Hype Cycle For Storage & Data Protection 2022
Background to the Gartner Hype Cycle For Storage & Data Protection The latest 2022 Gartner Hype Cycle report for Storage and Data Protection has just been published and

The Dummies Guide to Ransomware Resiliency for Enterprise Storage & Backup
It’s all about the data. One thing is clear. The “business value” of data continues to grow, making it an organization’s primary piece of intellectual property.
Are Your Backups Safe From Ransomware? Your 8-Point Checklist for Backup Security & Data Protection
The average cost of recovery from a ransomware attack has more than doubled in a year, according to a Sophos survey. The global report also shows

Analyzing The Security of Dell EMC Storage & Backup Systems – Four Highlights
In the first of its kind, Continuity published a new report that provides an analysis of the vulnerabilities and security misconfigurations of enterprise storage & backup

When, Why and How To Create A Secure Backup Strategy
Introduction When data is compromised, the last line of defense is your backup. In the past year, the tactics being used by cybercriminals have changed. And

Don’t rely on your Storage & Backup Vendors for Security
I hear this a lot: “Why do I need to scan my storage & backup systems for security risks? Don’t my storage vendors already do this

New Data Protection Methods and the Impact on Securing Storage & Backup
Written by CISOs, for CISOs This article provides highlights from our ‘CISO Point of View: The ever-changing role of data, and the implications for data protection
CISO Point of View: Discover how other CISOs deal with the complexity of data protection and storage security
Data plays an increasingly important role in the modern enterprise. With digitization, data comes much closer to the customer – with large amounts of data being

4 Predictions for storage and backup security in 2022
Cyberstorage gained more attention in the media in 2021 with the rise in data storage hacks, ransomware attacks, and cases of immutable storage erased. As these

The most critical – and overlooked – security issues facing financial services
A few words about the author: John Meakin is a seasoned and experienced CISO with more than 30 years of experience in various financial services companies,

Gartner Shines a Light on Storage Security
In October 2021, Gartner published its “Innovation Insight for Cyberstorage Solutions to Protect Unstructured Data Against Ransomware.” We were thrilled to see the authors shine a light on the need to put active defenses around a company’s most valuable asset – the data it houses in storage and backup systems.

Storage & backup security in the financial services and banking sector – Highlights from the 2021 survey report
The financial industry is rightfully alarmed by the increase in both the amount and sophistication of data-centered attacks – primarily ransomware. We’ve all read the news.

Storage security mythbusting: 4 myths CISOs still believe, and why they’re wrong
Experience is the mother of wisdom, or so the famous proverb goes. And there’s definitely something to that: the more of life we’ve experienced, the more

The Status of Storage and Backup systems related to the Log4J vulnerabilities
A new critical vulnerability (CVE-2021-44228) was identified in Apache Log4J – widely used by numerous applications, services and frameworks. This vulnerability received the highest CVSS severity score of 10.
Talk To An Expert
It’s time to automate the secure configuration of your storage & backup systems.